Introduction
dwepdump is a pcap based packet collection application modelled towards collecting packets for use with dwepdump for both brute forcing wep keys as well as collecting packets for use with the weak ksa attack. additionally you can use dwepdump to converge pcap logfiles for use with the weak ksa attack in dwepdump.
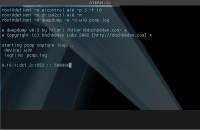
note: as of v0.2, only 3 key statistics are shown. generally, once all three of the key slots have reached 60 (0x3c), you should be able to crack the key with very little trouble. however, in many cases, > 20 (0x14) will suffice.
current features of dwepdump include:
 logging only weak keys for use with dwepcrack -w logging only weak keys for use with dwepcrack -w
 real time statistics on how many weak ivs have been found (n.x -> n:x when x >= 60 so you know when to start cracking :-) real time statistics on how many weak ivs have been found (n.x -> n:x when x >= 60 so you know when to start cracking :-)
 normal pcap dumpfile logging normal pcap dumpfile logging
 ability to specify the max packet size so you only capture small packets (so the cracking is faster) ability to specify the max packet size so you only capture small packets (so the cracking is faster)
 not needing to specify a device, so you can take multiple pcap files and filter them together into one (useful if you have a ton of standard pcap dumps and want to filter out the weak ivs, or converge weak iv dumps). not needing to specify a device, so you can take multiple pcap files and filter them together into one (useful if you have a ton of standard pcap dumps and want to filter out the weak ivs, or converge weak iv dumps).
 use of iv filtering methods outlined in "Practical Exploitation of RC4 Weaknesses in WEP Environments" for faster capture time. use of iv filtering methods outlined in "Practical Exploitation of RC4 Weaknesses in WEP Environments" for faster capture time.
Screenshots
Compilation
To compile dwepdump for a bsd operating system, simply review the default Makefile for any options you might want to change, and then run make.
$ vi Makefile
$ make
Installation
To install dwepdump, simply run make install. The Makefile will install dwepdump into /usr/local/bin by default and chmod/chown them to 700/root.wheel so you can only run it as root: (root is required to run dwepdump).
$ sudo make install
Running
There are a few command line options you can use when running dwepdump:
usage: dwepdump [-w [-s | -a]] [-m <max>] [-d | <device>] [<in> [...]] <logfile>
-w: log weak keys to logfile for use with dwepcrack -w (40-bit default)
-s: log packets that use 104-bit encryption
-a: log all packets intead of just ones with weak ivs
-m: maximum size packet to allow through
-d: specify that the device isn't specifed, just join the in files
For dwepdump to work, it requires you set your prism2 card into monitor mode:
$ sudo prism2ctl wi0 -m
However, you may want to make it only listen on the particular channel you're breaking wep on:
$ sudo wicontrol wi0 -p 3
$ sudo wicontrol wi0 -f 10
$ sudo prism2ctl wi0 -m
|
|